Proxy tools are the means to enhance your device security as well as usability without letting others know your device’s IP address. They are the handy tools that are befitting for many of the organizations.
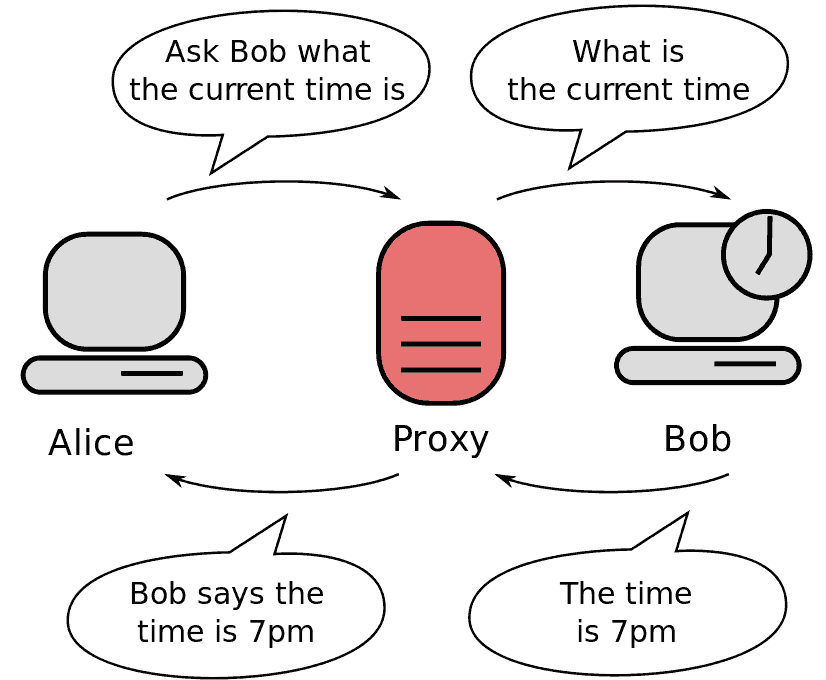
Proxy servers are primarily other systems which act as a hub to process Internet requests. They are basically an intermediary source, which serves on behalf of the clients seeking resources from other servers. They are used for various reasons, like putting browsing restrictions on employees, filtering web content, and allowing one to surf the Internet anonymously.
 They are used for fast, secure, and reliable system functioning. They hide the original IP address and will only show the IP of the proxy server. In this way, they offer more privacy while you are directly connecting to the Internet. There are a number of proxies that a person can utilize, depending on the user requirements. They are either available as free software downloads or as paid services.
They are used for fast, secure, and reliable system functioning. They hide the original IP address and will only show the IP of the proxy server. In this way, they offer more privacy while you are directly connecting to the Internet. There are a number of proxies that a person can utilize, depending on the user requirements. They are either available as free software downloads or as paid services.
Their integration allows computers to make indirect network connections between two networks. If anyone is using them, his system’s request will go to the proxy server first. The proxy server will then process the request further in requesting resources like web pages, games, and e-books available on the Internet. At the time of such a request, the proxy server will search the resources from the cache, and if they have been cached earlier, they will return to the client computers. If they are not cached before, they will connect the client computer to the relevant servers on the behalf of the client server.
The primary roles of proxy servers are to:
Provide web access
They are used to provide the remote functionality of web access. These are very useful for creating the connectivity within any corporate or organization. Many corporations run them to establish user to user connectivity, allowing users to share their ideas and plans safely with employees currently located outside the network.
Protection from threats
They are also utilized as a way to securing the contents of data transmission over the web. Many intruders try to hack connections in order to gain access to very important data (like financial details, corporate secrets, etc…). Proxies protect the client computer from this kind of attacks by hiding the true location of the data. They act as a barrier between corporate and potentially corrupted web applications for the same thing.
Authentication
Proxy servers are all about allowing access only to authorized users. They possess a tight authorization protocol and provide total security to your organizational network. Their network address translation ability helps corporations to secure the central server. They can also be combined with firewalls, which makes them capable of blocking even more web generated threats. They grant the access only to those systems which are authorized to share the connectivity with them.
Ultimately a proxy server is an application designed for processing the request of a client computer, and it masks the true IP address of the client computer. In this way, you as a client can hide your identity from the world. They are very useful for the business organizations. Many are available as a software free download. It is recommended that you evaluate their features before deciding to integrate one into your system, in order to make sure it will actually serve the purpose you want. Be aware that there are malicious sites offering free software downloads of proxy server software in order to breach your computer security. Make sure you only download from a trusted website.
This was a guest post by Kanika Ahuja. Kanika is a content writer who tries her best to share important knowledge about topics like free android apps to download, free game apps for iphone and free mobile apps to download.