There are many benefits of having VPN services for your business. As a user looking for a reliable Virtual Private Network provider in the market, the first thing one would notice is the large choice of providers available in the marketplace. A person can sometimes get…
Category: Networks
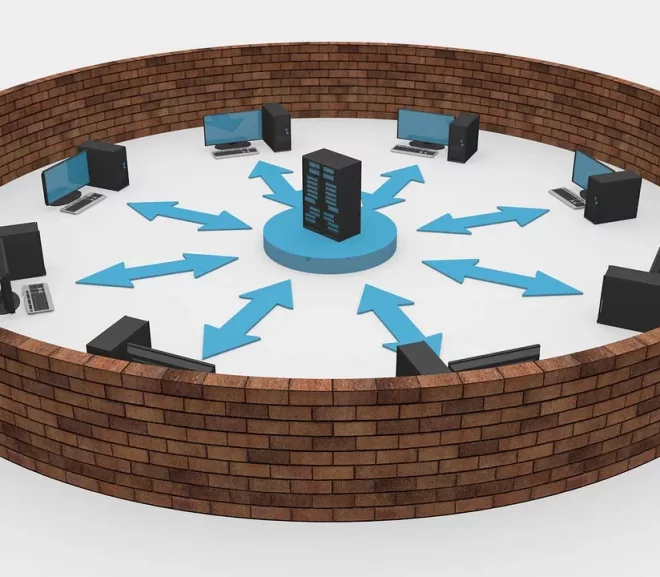
Those who deal with the computers and networks in their line of work are sure to use and hear the word several times during their work. But for the laymen, it is a puzzle to understand this term. So, here we bring to you an…
Mobile VoIP applications that have been developed, cater to the mobile device market. Having made a stable base within the communication industry, the VoIP mobile dialers have been delivering a more beneficial communication experience. When VoIP was initially introduced into the market under the communication…
Firewall implementations are available today from a wide array of vendors. With the ever-increasing awareness of network security and the costs of lost information, many new firewall implementations continue to emerge. This article discusses Black Hole, a firewall produced by Milkyway Networks Corporation in Ottawa,…
As always, the very real danger is that managers themselves will become seduced by the new technologies and then appreciate them only superficially and misunderstand their true purpose and potential. Indeed, a full, in-depth evaluation and understanding of the business processes that make a company…
The United States of America, being the most powerful economy in the world, its citizens heavily rely on technology for almost all aspects of life. In fact, the whirling dynamics of a volatile economy and a vulnerable society has turned data into the new age…
Located and managed application services are not really new technologies – they are very similar to the service bureau computing types of years past, in which green-screen dumb terminals had been connected via cellular phone lines to big host systems located “somewhere else”. These days,…
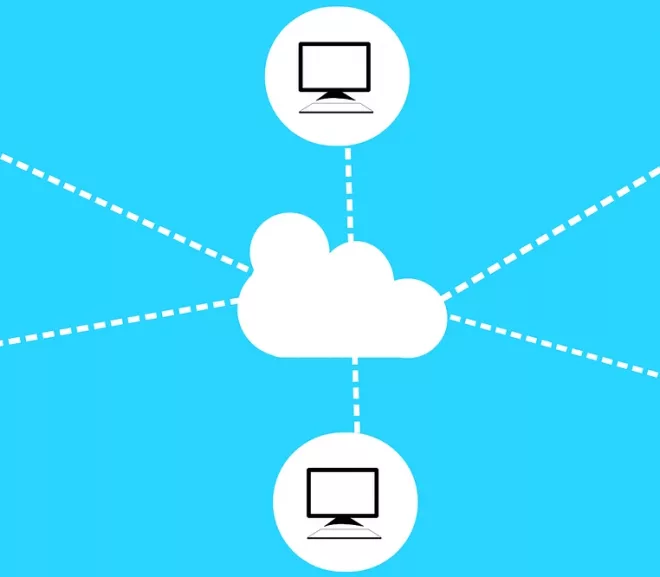
Moving to the cloud is a decision which can be taken after considering the local setup you have. Cloud is the latest technology which is creating great results for companies. The most important and crucial aspect of this technology is the adoption or migration process. In…
It is very important to take the proper security measures for the safety of your wireless network. Doing this is the only way to avoid the chances of attack by hackers and other web intruders. Wireless connectivity is becoming a more and more convenient choice…
Proxy tools are the means to enhance your device security as well as usability without letting others know your device’s IP address. They are the handy tools that are befitting for many of the organizations. Proxy servers are primarily other systems which act as a…